This article will introduce how to use Oracle Cloud to build a highly available, cross-regional system. We know that high availability describes a system that is available most of the time and can provide us with services. High availability means the service is still available even during a hardware failure or system upgrade. Eliminate single points of failure through proper use of deploying instances across multiple availability domains
We’ll create load balancers in three different regions, each with two servers at least behind them that use the same application and expose the same ports.
Let’s take a look at our system design architecture design first.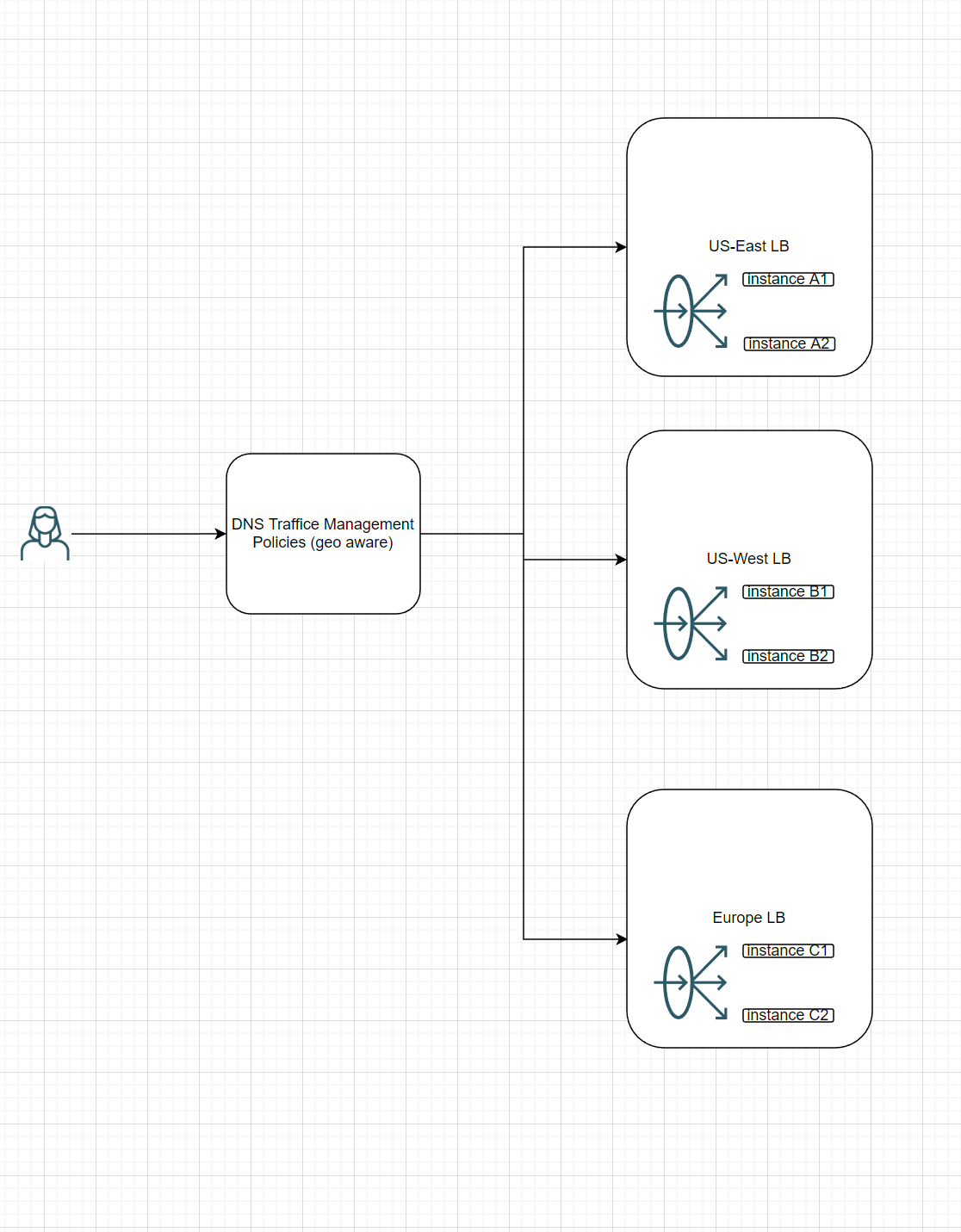
In this architecture, We create three load-balancers distributed in the us-west, us-east, and Europe regions.
So we have three regions with identical resources. And the traffic will route to the specific load balancer with rules. And fallback to other load balancers.
We’ll show how to create this architecture step by step